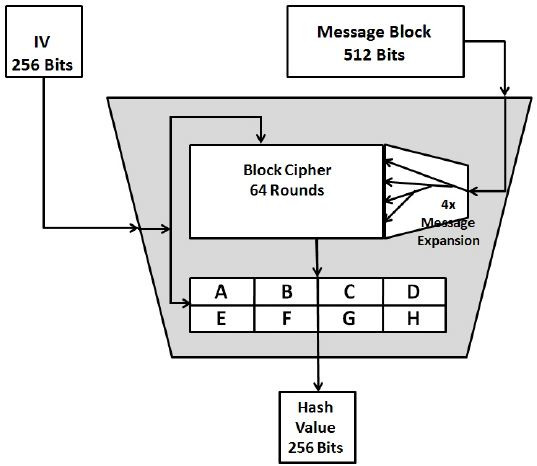
SHA256 Introduction
Cutting edge cryptography is used to secure Bitcoin. It uses a cryptographic function called SHA-256 to secure all of the information. You can take characters, words, or numbers to use as an ‘input’. The Input goes into one end of a ‘magic box’ and gets changed so that something different comes out the other side. If you always put the same thing into the box, you will always get the same changed thing coming out the other side. But you cannot reverse the function. You can think of it like cooking. If you take an egg and put it in a hot pan, it will cook. You’ll always get a fried egg. You cannot take a cooked egg and uncook it. .SHA means “secure hash algorithm” and was developed by the NSA. It is completely open for anyone to see how it works and to use. This cryptography can be as simple or as difficult to explain as the instructor chooses. There are many good analogies to use. Learning about these things teaches about mathematics in a very practical way. By learning this, students can be challenged to think about puzzles. It’s fun, challenging, and cool. It stretches the imagination.
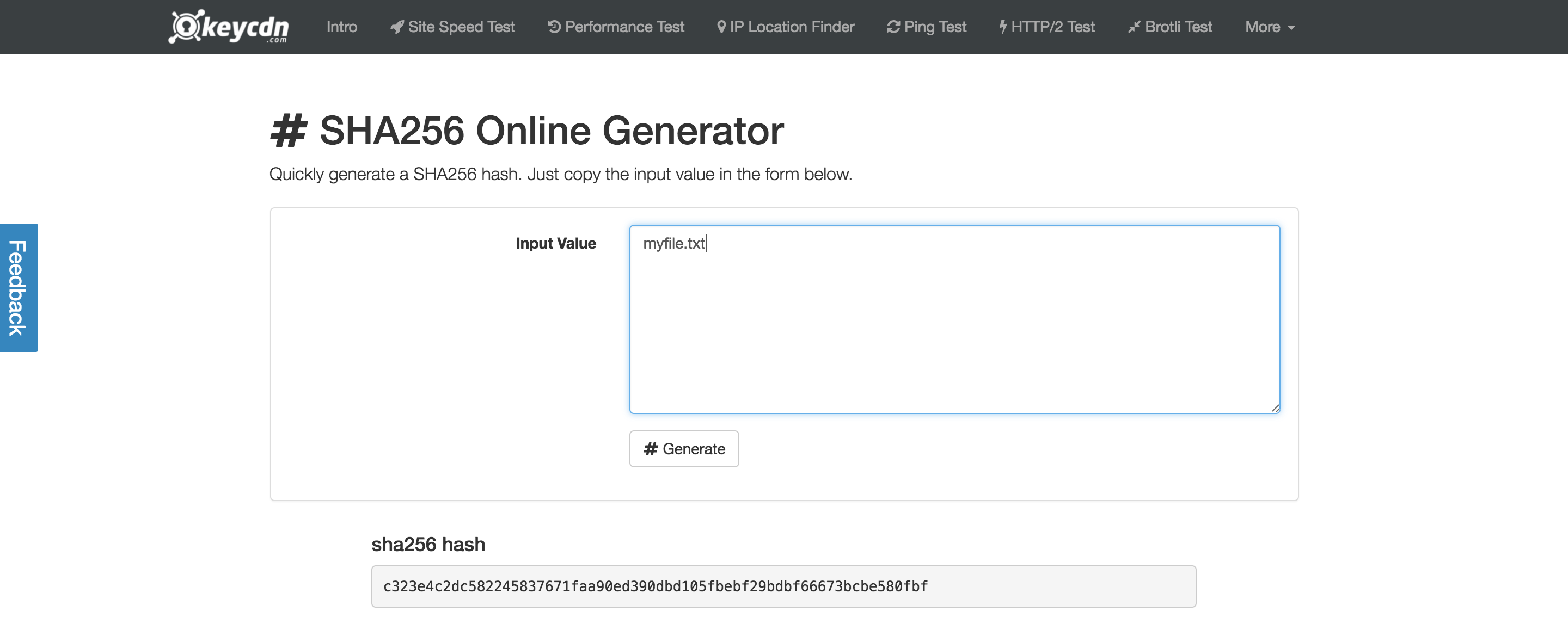
Try SHA256
You can actually try out this function for yourself by visiting this website.
1. Type your input into the box, then click “compute” to get your output.
2. Save your first output. Now change 1 character from your first input and compute. See that you get a completely different output.
3. Now type your first input once again and click compute. If you saved your first output, you’ll see that it’s always the same output if you use the same input!
Give it a try!
SHA256 Code:
The coding for SHA256 is available for anyone to copy, use, and see!